CBCTF躲猫猫题解
前言
拖了好久好久的题解,出完题整个人都会变得懒得复盘,可能出的时候都是一整个稀里糊涂的状态,想着怎么做到尽可能知识点简单&有趣&能做出筛选,但最终结果好像不是很尽如人意,四道题第一天就上了到最后也没什么人在看,算是整了盘大的。招新赛那天正在跨年,当时早上去老婆大人买了三大袋零食,下午一边双扣一边运维,看着其他方向的题矻矻被出,密码题无人问津,脑子都坏掉了。带着队友去吃了顿鸡啤咯哒以消解愁绪,也算过了个难忘的新年吧。
Anyway话不多说,就让厨师把一整道菜都端上来瞧瞧吧。
躲猫猫1
跨年夜当然少不了团建活动!
冬天雪花飘飘正适合玩躲猫猫,为配合赛博主题,0RAYS的每个队员身上都带着一小段flag,拼起来就可以兑换过年大礼包!你毛遂自荐作为抓捕者,于是队员们悄眯眯地藏起来了。
夜晚静悄悄的,你数完数踏出起点,影影绰绰看到几个人影......
1 | import random |
humb1e's part
1 | #学活广场 humb1e似乎在旗杆背后探头探脑 |
Roll了一个多项式商环R,然后去在环上进行运算。令R函数表示随机,那么此时我们对于flag的不同位数,有 \[ \begin{gather} flag[i]=1:humb1e^{1500*R(h,u,m,b,1,e)} \\ flag[i]=0:Random \space element \ \end{gather} \] 那么显然,在数据当中出现次数大于1次极有可能等价于flag[i]=1(因为modulus的度有30),统计一下就可以恢复flag串。
1 | from Crypto.Util.number import * |
Ech0's part
1 | #都放假了四教还亮着灯?抓到Ech0在躲猫猫的时候偷学密码! |
这个部分的处理更加清晰,即随机roll一个数、并计算它的欧拉函数,有 \[ \begin{gather} flag[i]=1:Φ(Random \space number) \\ flag[i]=0:Φ(Prime \space number) \end{gather} \] 那么这个时候我们需要进行两层判断,第一层是判断所给数值加上一是否为素数,第二层是判断素数的bit数是否为100。代码如下
1 | from Crypto.Util.number import * |
此时不排除随机数就是bit数为100的素数,因此可以debug得出正确的flag
1 | #!Hope_y0u_can_h4ve_ |
Z3r0's part
1 | #雪下得好大,花圃周围的亮白色身影是Z3r0吗 |
对于flag二进制位上的数字,令Q为随机素数,有 \[ \begin{gather} flag[i]=1:31337^{65537} \enspace mod \enspace p·Q\\ flag[i]=0:31337^{65537} \enspace mod \enspace Q_1·Q_2\\ \end{gather} \] 两个flag位等于1的数据\(c_1,c_2\)有关系如下 \[ \begin{gather} c_1=31337^{65537}+k_1pQ_1\\ c_2=31337^{65537}+k_2pQ_2\\ \end{gather} \] 因此可以得到关系 \[ c_1-c_2=(k_1Q_1-k_2Q_2)p \] 然后玩法就多了,可以考虑用gcd把p求出来然后求证每个数据在\(GF(p)\)上是否与\(31337^{65537}\)等价,这样在求出p以后每个数据都只使用一次,就能够完成最后flag的求解。
1 | from Crypto.Util.number import * |
躲猫猫2
Humb1e,Ech0,Z3r0藏得都太草率了,显然没有把游戏放在心上。你语重心长地批评了他们一顿,踏上寻找其他人的旅途。
这下游戏就没有那么简单了。已经拿到一个新年大礼包的你能否再次创造奇迹呢?
1 | import random |
gtg's part
1 | #你惊异地发现,树丛里黑糊糊的枝叶居然有点神似gtg的辫子 |
定义了两个矩阵群,并令两个矩阵群的生成元数值相同,群a位于\(GF(149)\),群b位于\(GF(163)\),数据与flag位的关系如下 \[ \begin{gather} flag[i]=1:M=CRT([m^{r_a},m^{r_b}],[149,163])\\ flag[i]=0:M=RandomMatrix \end{gather} \] 我们把CRT过程分成两半来进行考虑,\(M\)矩阵模\(149\)时得到矩阵\(m^{r_a}\),同理模\(163\)时得到矩阵\(m^{r_b}\),那么令\(m\)在a中的阶为\(oa\),令\(m\)在\(b\)中的阶为\(ob\),对于flag为1的数,把它们放在模p下进行以oa为幂的幂运算,放在模q下进行以ob为幂的幂运算,可以得到下列式子 \[ \begin{gather} M^{oa}=m^{ra*oa}=E~mod~p\\ M^{ob}=m^{rb*ob}=E~mod~q \end{gather} \] 因此在两边都会得到单位矩阵,通过这个性质我们可以区分所有的数据。
1 | from Crypto.Util.number import * |
同样是debug一下,还原出flag
1 | b'CBCTF{W1sh_Y0ur_N3xt_Y3' |
beeee's part
1 | #前两天刚考完研,图书馆难得清静,你在9楼搜寻,只见角落闪烁着微光。好像是beeee! |
基于pallier,把pallier里的若干参数都替换成了p,底数也从pq替换成为p^2,加密消息不变。 \[ \begin{gather} flag[i]=1:ppallier(m,p)\\ flag[i]=0:RandomNumber \end{gather} \] 首先对于ppallier加密的数据,有 \[ c=(p+1)^{km}r^p~mod~p^2\\ \] 根据二项式定理, \[ (p+1)^{km}=1+kmp~mod~p^2 \] 而后半部分的随机数相关部分可以通过\(p-1\)的幂运算消除,类似Z3r0,进行相似的分析, \[ \begin{gather} c_1^{p-1}=1+k_1mp(p-1)=1-pk_1m~mod~p^2\\ c_2^{p-1}=1+k_2mp(p-1)=1-pk_2m~mod~p^2 \end{gather} \] 因此这里其实就又只是一个gcd,不同点在于这里要筛出一个为1的点,拿三个点进行多次比较,如果gcd值够大就记为1。啊哈哈,真是炒冷饭大师啊。
1 | from Crypto.Util.number import * |
Seg_Tree's part
1 | #看上去有人卡视野藏在协会天台上。你走了过去,Seg_Tree正在假装自己是一颗树。 |
考的是CFB模式里有个特性,即移位寄存器使用密文填充。
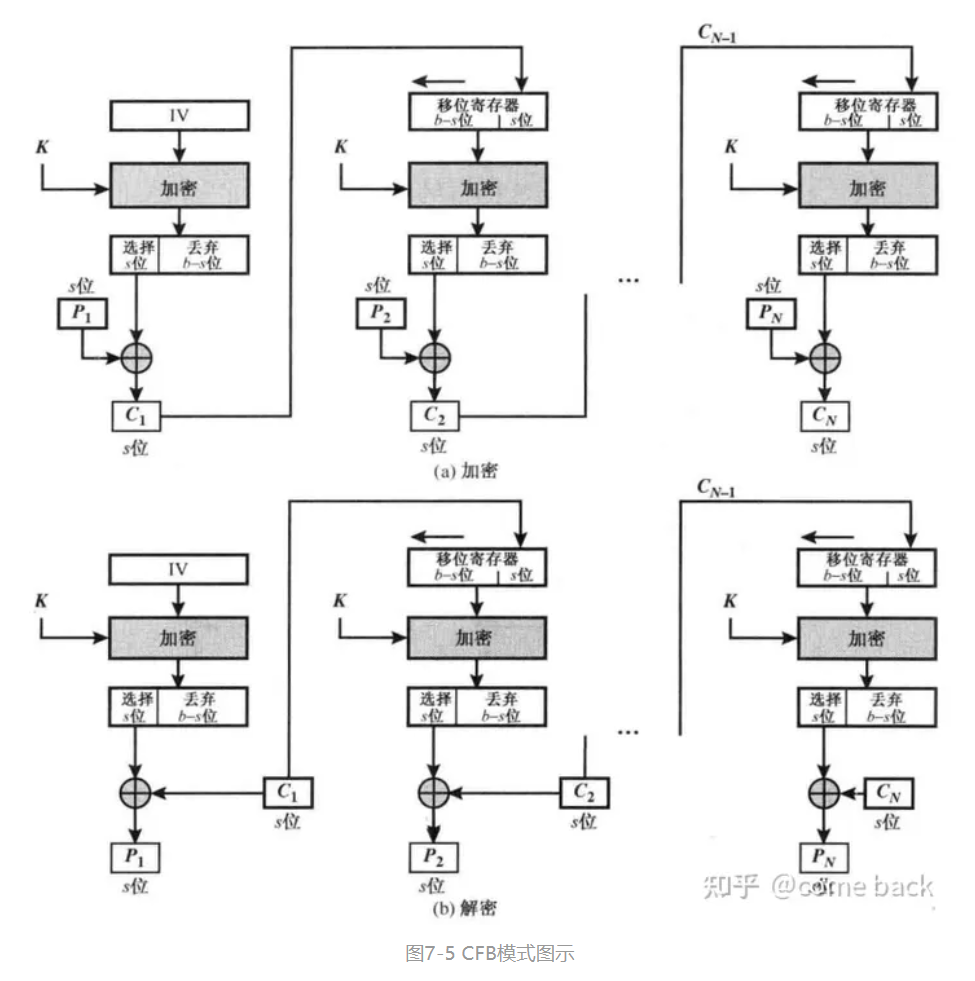
由于移位寄存器中填充的是密文,因此当密文以16byte为单位进行重复时,移位寄存器中每隔16byte也会出现一次重复,因此如果结果中的第17个byte和第33个byte相同,则说明使用的是decrypt。题目中特意卡了一个33,目的也是在于做出提示。
1 | from Crypto.Util.number import * |
躲猫猫3
你花了点力气找到了gtg,beeee和Seg_Tree。手握两份新年礼包的你显然已经是整个协会中最富有的哥们儿,你一边畅想着未来的幸福生活和完美外设一边哼哧瘪肚在冬日里前行。
剩下的人都是难找的茬子啊......
不过你坚信这一切难不倒你。
1 | import random |
Art0ne's part
1 | from secret import p,q |
经典copper,一个类似已知p高位的情况,给出的条件可以简化成\(kp+p_h\)的形式,所以直接拿比较宽松的参数去打就行。
1 | from Crypto.Util.number import * |
奶茶's part
1 | #你找遍了学校,最后在弗雷德二店的古茗二楼意外找到了奶茶并宣判他犯规 |
相当于每个flag的位数都和最终的数据有两重关系,第一重关系在于当前flag的位数会影响异或运算的结果;第二重关系在于当前flag的位数会影响异或bit串的生成。当当前位置bit数为1时,01比为5:3;当前位置bit数为0时,01比为3:5。
而我们已知第一个bit一定是0,可以利用的点在于,两个bit数相同的位置生成的异或bit串重合度从概率上来说显著高于两个bit数不同的位置生成的异或bit串重合度。那么我们可以设计一种算法对这种性质加以利用:
- 将与第一个bit所生成的bit串重合度最低的若干个bit串所在序号暂时标记为'1'
- 我们有'1'中多0少1的性质,由于'1'集合中'0'占比较大,说明各个bit中与0异或的可能性较大,因此我们统计当前'1'集合中各个bit的出现1的概率,出现1概率较大,说明当前位置很可能是'1',反之就说明当前位置很可能是'0'。这样,我们就可以更新得到一个更大的'0'集合和'1'集合。
- 对于'0'集合,将它的所有位与1异或,转变成一个符合'1'集合的特征的数据,不断缩小阈值、扩大集合,最终恢复所有位数。
小插曲:居然发现了测题的时候留下的代码,这样就省去了重写的功夫,不过看起来有些冗余,就勉强勉强。其中a变量填上题目给的数据。
1 | a = |
1manity's part
1 | #1manity藏在师生驿站,跨年夜店里没有值班,乌漆嘛黑的还带个笨蛋智能门锁,要不是你渴了进去买杯饮料还真的找不到他 |
给了若干个4×4矩阵,我们需要从中找出由七个未知矩阵进行线性运算构成的矩阵。题目当中我们已知尾byte为'}'=0b1111101、首bit为'1',因此手上正好7个已知1bit。
我们把矩阵看作长度为16的向量,那么就能够知道,只要它们线性无关,由于剩下的向量与这些向量都由同样的基构成,因此将7个已知向量与一个验证向量拼成的8×16的矩阵的秩仍然是7;反之,如果秩为8,说明验证向量是随机生成的。
1 | from Crypto.Util.number import * |
躲猫猫4
说来奇怪,在1manity,Art0ne和奶茶之后,你找遍了一整个学校都没能找到剩下的人,只能启动planB,使用你长期修炼凝结而成的密码解析技巧去把他们的参数调出来一一分析。
你以为你稳操胜券,但定睛一看,JBNRZ居然开了外挂卡在墙的里面!
他也把misc技巧带出了虚拟世界!
这个发现震惊了你的世界观,随着你打开每个人的视角偷看他们的位置,你的下巴不知不觉掉到了地上。
1 | import random |
JBNRZ's part ———有待更新·标记 5/9
1 | #JBNRZ开了修改器把自己卡在七教二楼阳台的墙壁中间。你就算知道他在哪,也没法摸到他。 |
Pankas' part
1 | #pankas用注释符把自己注释掉了,你必须使用一些过滤手段停止他的作弊行为。 |
犹记得当时出的时候特意卡了一些板子,但是具体过程已经说不上来了。调用的是Niederreiter system,隐私矩阵S和H已经完全给出,同时知道加密结果H_*v,权重在目标范围内,P矩阵只对解码结果的顺序有影响,因此此时整个加密系统在攻击者的眼中是透明的,可以使用伴随式解码直接进行攻击。
当然,题目里的error数值太小以至于可以用格子直接打出来,是一个大大大大非预期。
具体实现还是没忍住直接调了sageapi哈哈哈哈
1 | from Crypto.Util.number import * |
v0id's part——有待更新 标记 5/9
1 | #v0id通过某些方法修改了自己的人体结构,看上去需要经历一些反混淆反编译才能重现世间。 |
串了超椭里相对常见的两个考点,也算是给自己好好复盘下。